Admin Content
12d Synergy optionally allows users to log in via two-factor authentication that is set up by the 12d Synergy Administrator. The 12d Synergy Administrator can choose to provide the second level of authentication via email or a secondary device to all users or specific users.
Two-factor authentication provides additional protection for your server by performing a two-level verification while accessing the application. The two levels of verification are as follows:
A correct username and password.
A one-time password (OTP) that is provided by either an email or by registering a secondary device with a Third-Party Authenticator application, such as Microsoft Authenticator or Google Authenticator.
If your username and password are compromised, your data is still secure, as the external party does not have access to the OTP.
Your 12d Synergy Administrator can enable two-factor authentication for all users globally or handle it on a per-user basis.
Only the 12d Synergy Administrator can set up two-factor authentication for users.
You can log in to a 12d Synergy application using one of the following three modes of authentication. The login process depends on the authentication mode you select.
Windows Authentication
Custom Authentication
Single Sign On
The built-in two-factor authentication of 12d Synergy is NOT applicable to SSO users.
1.1. How to Enable Two-Factor Authentication for All Users
In the 12d Synergy Administration application, select the Users tab > Two Factor Authentication tab.
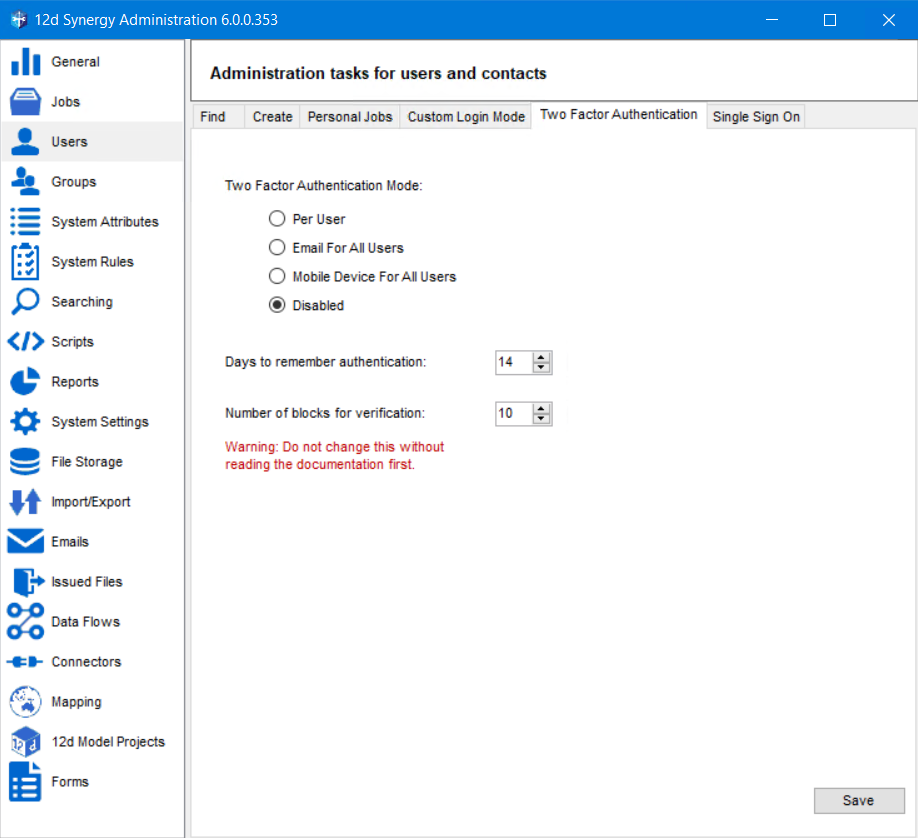
Do one of the following:
Select the Per User option to enable the 12d Synergy Administrator to set a user-specific two-factor authentication system.
Select the Email For All Users option to enable all users to receive the authentication code via email.
Select the Mobile Device For All Users option to enable all users to receive OTPs via an Authenticator app installed on their mobile devices.
Select the Disabled option to disable the two-factor authentication system for all users
Select the number of days you want the system to remember the authentication from the Days to remember authentication list. After the selected number of days has passed, you will need to complete two-factor authentication again to access the system.
If there is a difference between the time on the system on which the Client is running and the time on the secondary mobile device, then allow for an extended time frame for keying in the OTP by choosing the time blocks in the Number of blocks for verification list.
Third-party authenticators use time to generate one-time passwords. This means the mobile device time and the server time must be closely aligned, or the user may not be able to sign in. This can be adjusted by changing the verification time blocks
Each time block is a 30-second frame. Calculate the time blocks needed based on the time difference between the system time on which the Client is running and the secondary mobile device's time. The user can enter the code within the time frame chosen, which is the number of blocks multiplied by 30 seconds.
The more time blocks you allow, the greater the security hole, because it creates a lag between OTP generation and use. A very large time window may allow anyone to copy the OTP if they gain access to a user’s device and log in later.
By default, the Number of Blocks for Verification list is set to 10. It is a good practice to set the Number of Blocks for Verification to a maximum of 20, which is 10 minutes.
You should sync your server and secondary devices with the same Time Server, such as the Microsoft Time Server. This way, the time on both devices will be the same, and you can allow fewer blocks of time for verification. Thus, making the system more secure.
1.2. How to Enforce Two-factor Authentication for Specific Users, the time on both devices will be the same, and you can allow fewer
In the 12d Synergy Administration application, select the Users tab > Find tab.
Search for the required user by entering the required parameters and clicking the Find button.
The Edit Users window is displayed with the user(s).Select the required user(s) and click the Edit button.
The Edit a User window is displayed.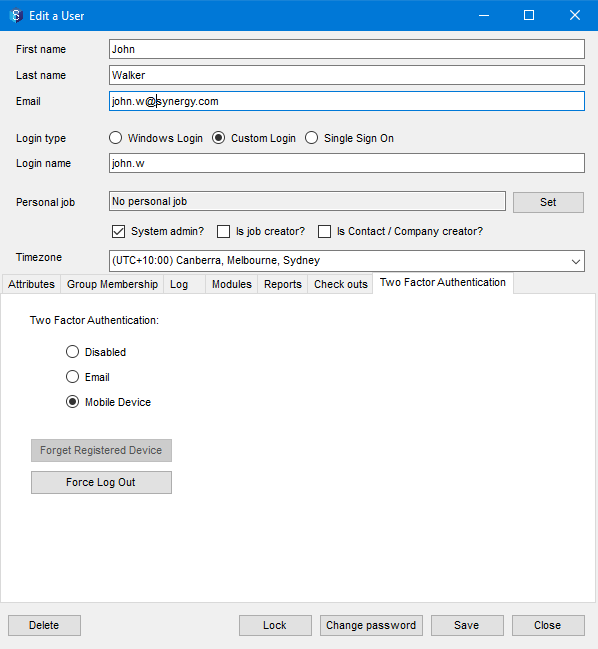
Click the Two Factor Authentication tab.
This tab is disabled if you are an SSO user.
Do one of the following:
Select the Disabled option to permit the user(s) to log in without two-factor authentication.
Select the Email option to enable the user(s) to log in with two-factor authentication by receiving the OTP via email.
Select the Mobile Device option to enable the user(s) to log in with two-factor authentication by receiving the OTP via a secondary device.
Click the Save button.
The two-factor authentication settings are saved for the user(s).
1.3. How to Change the Registered Secondary Device
In the 12d Synergy Administration application, select the Users tab > Find tab.
Search for the required user by entering the required parameters and clicking the Find button.
The Edit Users window is displayed with the user(s).Select the user whose secondary device needs to be changed, then click the Edit button.
The Edit a User window is displayed.Click the Forget Registered Device button.
The selected user’s registered device for two-factor authentication is disabled, and the user is logged out of the 12d Synergy Client application. You can then register a new secondary device for two-factor user authentication.In case a user needs to forcefully log off the 12d Synergy Client application, then the 12d Synergy Administrator can click the Force Log Out button in the Edit a User window for that user.
Whenever a change is made to any of the two-factor authentication settings, you will be prompted to enter an OTP. The OTP is sent to you either on your secondary device or on your email, based on your two-factor authentication settings.